MacroVirus
Macro Virus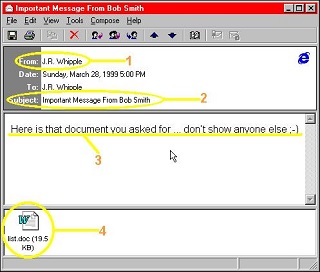
A macro is a type of script that automates repetitive tasks in Microsoft Office applications
(such as Word, Excel). Macros are a useful way to make some tasks perform more efficiently.
Unfortunately, macro viruses perform the same functions as macros, but they tend to
be harmful. For example in March 1999, the Melissa macro virus caused Microsoft to
shut down the company's entire email service. Melissa spread rapidly and arrived
as an attachment with the subject line "Important message from [name of someone]."
The body text read, "Here is that document you asked for...don't show anyone else."
If the recipient opened the attachment, the macro virus infected the computer and
carried out a series of commands. Melissa was a fast-spreading virus, infecting more
than 100,000 computers in the first few days. Macro viruses remain a threat today,
but the good news is that the user must perform some action for the virus to be activated;
therefore, educating users not to open the attachment is essential. Most modern operating
systems and office suites do not automatically run macros, so the threat from macro
viruses is reduced.
Defenses
User Awareness and Information Security Training: Empowering the user is always the first line of defense. Diligent and educated
users will automatically be wary of file attachments. While macro viruses require
user intervention, giving permission for the code to run, social engineering tactics
attempt to entice and trick the user into performing this step. Strong user awareness
and training is paramount - users must be diligent and even a little fearful when
it comes to email attachments.
Anti-Virus / Anti-Malware End-Point Protection: Not just for viruses, anti-virus software can also scan Microsoft Office file type
attachments such as Word documents and Excel spreadsheets. There are many free anti-virus
solutions for home users, for Windows, Linux and Macintosh computers. Regardless
of the operating system you use, anti-virus is a must-have. This protection provides
a second layer of defense, and will intervene if the computer user (or some background
program process) attempts to execute or interact with a virus. Furthermore, anti-virus
solutions typically quarantine the malicious program, placing it in an isolated location
which can allow for further review by a technician or information security practitioner.
